More than a month after the grand finale of the Ekoparty Security Conference 2012 and with a little time to better understand all the big things that came out of the 8th edition of the EKO party. We did this review for everyone that came and for those that weren´t able to make it unfortunately.
Like we´ve grown accustomed to, the conference was split into two parts with two days of training and three days of talks (Sep 17th to the 21). We were fortunate enough to return to the Centro Cultural Konex, where we had over 1,500 attendees and had to use both the full auditorium and all additional seating.
The staff like always surprised us with a bit of a show with a ¨special theme¨... They didn´t disappoint with a spaceship falling to the stage with parachutes. Of course, like any spaceship this one had an astronaut (and a chimp!) and somehow a laser shooting robot got involved as well.


Like every year, people were really looking forward to the event. We had the traditional CTF (capture the flag), Lockpicking and lots of stands from sponsoring with fun games (a couple with bars to loosen up the crowd) and later very cool speakers. We had many speakers from Latin America who are well know abroad and additionally we were able to have internationally recognized speakers come from outside the region as well..

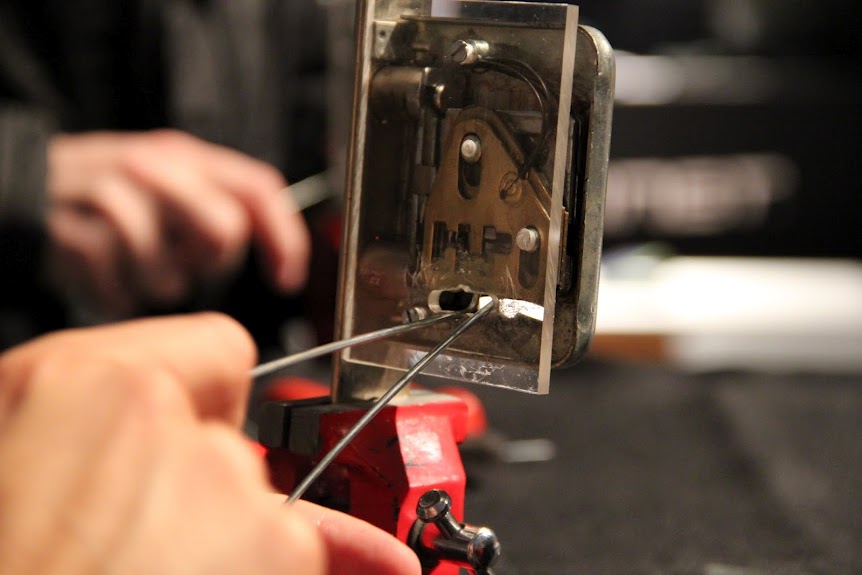
After finishing up the talks, everyone broke into workshops which normally lasted about two hours. Some worth highlighting were Fernet Overflow from Enrique Lurleo and David Arch (Argentina being one of the spiritual and commercial homes of fernet), Forense en dispositivos Android given by Julian Zarate, and the VERY popular lockpicking workshop by Juan Urbano Stordeur. Check out the pictures!






After we continued with a talk from Matias Eissler and Andres Blanco titled “One firmware to monitor ‘em all”. In this talk they showed how to manipulate the different firmwares especially those used in wireless cards, smartphones and tables and how to create a Fake AP.

Then we had a talk titled Sql Injection from zero to pwn by Matias Katz and Maximiliano Soler who showed how to take control of a server from scratch through the tool HTEXPLOIT coded in python, which they are thinking about adding more funcions like map, dirbuster, metasploit among others.







Right after, continued the Argentine Agustin Gianni, who had already been a speaker a number of times in the EKO party with “Trace Surfing”. He spoke about automated techniques to improve the required times while investigating inverse engineering for software.







Here you can find the slides acá (here) that show off a little more of the EKO party and explain a little better the talkes.


Like we´ve grown accustomed to, the conference was split into two parts with two days of training and three days of talks (Sep 17th to the 21). We were fortunate enough to return to the Centro Cultural Konex, where we had over 1,500 attendees and had to use both the full auditorium and all additional seating.
The staff like always surprised us with a bit of a show with a ¨special theme¨... They didn´t disappoint with a spaceship falling to the stage with parachutes. Of course, like any spaceship this one had an astronaut (and a chimp!) and somehow a laser shooting robot got involved as well.
Like every year, people were really looking forward to the event. We had the traditional CTF (capture the flag), Lockpicking and lots of stands from sponsoring with fun games (a couple with bars to loosen up the crowd) and later very cool speakers. We had many speakers from Latin America who are well know abroad and additionally we were able to have internationally recognized speakers come from outside the region as well..
#Day 1
The first day we thought we were going to have some complications because of the rain, but everyone to their credit came with a big smile on their face. As in past editions, this part was mostly workspots and had only one talk about the EKO party kick-off.
This talk was given by Cesar Cerrudo and was called “Cyberwar para todos” (Cyberwar for all). The talk like always made us think and reflect about current events in the industry. It made us question how much we know about cyber weapons. Should we take them seriously? What are the problems posed to Argentina and around the world.
After finishing up the talks, everyone broke into workshops which normally lasted about two hours. Some worth highlighting were Fernet Overflow from Enrique Lurleo and David Arch (Argentina being one of the spiritual and commercial homes of fernet), Forense en dispositivos Android given by Julian Zarate, and the VERY popular lockpicking workshop by Juan Urbano Stordeur. Check out the pictures!
Luckily the workshops were quite busy and we were able to show off for the first time in the EKO Party how to break locks with bike spokes. For me it´s pretty interesting because who doesn´t have one of these in their house?
And of course we couldn´t forget the good old-fashioned wardriviing, around scenic Buenos Aires making a router map. Thanks to having done this in past years we were able to see that more people are using passwords for their routers and are using better algorithms to protect them. We finished off the wardriving in a bar named Roots were we were able to eat some much needed pizza and sip on a few beers.
#Day2
The second day began with a lot of enthusiasm and excitement. We started off with the foamous CTF (capture the flag) but everyone was already pretty psyched with pre- talks with A LOT of action.
The second day began with a lot of enthusiasm and excitement. We started off with the foamous CTF (capture the flag) but everyone was already pretty psyched with pre- talks with A LOT of action.
The First Talk was Inception of the sap plataform’s brain: Attacks to sap solution manager” done by Juan Perez Etchegoyen and was about how to hack into the SAP Solution Manager through various attack vectors.
After we continued with a talk from Matias Eissler and Andres Blanco titled “One firmware to monitor ‘em all”. In this talk they showed how to manipulate the different firmwares especially those used in wireless cards, smartphones and tables and how to create a Fake AP.
Then we had a talk titled Sql Injection from zero to pwn by Matias Katz and Maximiliano Soler who showed how to take control of a server from scratch through the tool HTEXPLOIT coded in python, which they are thinking about adding more funcions like map, dirbuster, metasploit among others.
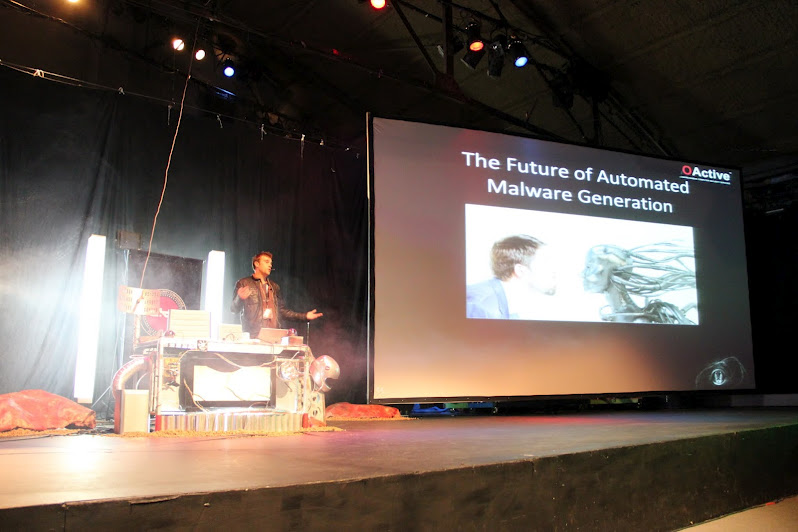
Right before lunch we had a talk from Stephan Chanete “The future of automated malwere generation, the R&D director of Ioactive who showed ¨exploits as a service¨, which referred to automated malware and how to evade antivirus software
After a quick bite to eat, we got to “Fear and Loathing in Java¨ given by Esteban Guillardo which showed a path of vulnerabilities of Java from its inception up to the present day.and how to exploit them. This talk had a bit of an unexpected spicy sauce when surprisingly a mariachi band (in the middle of the presentation) sang a love ballad in his honor.
Later we continued with Rahul Sasi “Fuzzing DTMF Input Processing Algorithms”, where he talked about how to code tones of DTMF (Dual-Tone Multifrecuency signaling) and how to alternate IVM terminals, showing how to saturate one of these with a massive influx of 1´s.
Lastly, as the day was finishing up came a a talk from Alfredo Ortega and Sebastian Muñiz “Satellite basebands mods: taking controll of the InmarSat GMR-2 phone terminal”, who demonstrated how to modify the firmware through only a cable usb and the impact this can have. With the use of sniffing and injection pacets between the telephone and the satellite.
To conclude the day we had relaxed with a few drinks in the Konex Cultural Center chatting a bit and meeting new people. While all of this was happening we had another a unexpected treat when an engineer from ITBA (Dan Etenberg) made his very own tesla coil and plane turbine. He had a lot of fun showing us how to light up the neon sign of the EKO and shooting fire from the turbine.
#Day 3
As the last day approached we had mixed feelings. On the one hand, we were anxious because there were still really good talks and always they try to save the best for last. At the same time we were a little down because, it´s something we look forward to the entire year and it was already winding down.
The first talk was presented by ¨The Gruqq¨ dealing with the topic of OPSEC:”Because jail is for wuftpd”. He showed the accusations of hackers through central intelligence systems. He showed how best to cover your trails and sensitive information through software and various techniques.
Following Agustin, we had the internationally recognized, Lorenzo Martinez (one of the writers of securitybydefault), presented “Welcome to your Secure /Home, $User”. This talk was very interesting demonstating how to apply biometrics, utilize cameras, facial recognition with a date base, connected alarms TCP/IP, third party knowledge, etc.
After lunch, there was 4140 Ways your alarm system can fail by Babak Javadi where Babak and his coworkers showed us that security alarms in the office or home are not really so secure. They demonstrated how to obtain user passwords with brute force. It reminds us that it´s good to keep in mind physical security and infrastructrure.
The second last talk was from Ravi Borgaonkar titled “Dirty use of USSD codes in cellular network” and it dealt with an introduction of contents (USSD) to show us later how to exploit the Android operating system. He concentrated especially on the Samsung Galaxy (SI SII SIII) Line where we were able to see how to exploit the device with malicious code. This way you could restart the cell and block the SIM by entering invalid PUKs.
Finally we got to the much anticipated talk from Juliano Rizzo and Thai Doung where last year they had really impressed us with BEAST. This year they showed a very serious error in the TLS protocol and how to exploit it to obtain cookies. There were a couple technical problems and the people were a little bummed they were not able to see the demo live. But then appear Ice-Bolt and his Chimpanzee Astronaut and that left everyone happy and smiling.
Here you can find the slides acá (here) that show off a little more of the EKO party and explain a little better the talkes.
While of course the emotions are bitter sweet because really it is a labor of love. We finished off with a bang with awards for the different stands, the lockpicking workshop and juicy awards of the CTF (for the first three finishers). The prizes were training and cash making us the first conference in Latin America to give such a large cash prize.
Really we have to thank the EKO planning staff that really did an incredible job and had been working hard for months to make sure it was a success. To everyone involved merchandising, security, catering, you guys all do a great job making it more than a security conference but a security fiesta!
See you next year!
Thanks for the photos Day 1 http://bit.ly/NL4qH0 - Day 2http://bit.ly/NL4tTf - Day 3 http://bit.ly/NL4uGM
Juan Urbano Stordeur.
ليست هناك تعليقات:
إرسال تعليق